What is Authorization policy?
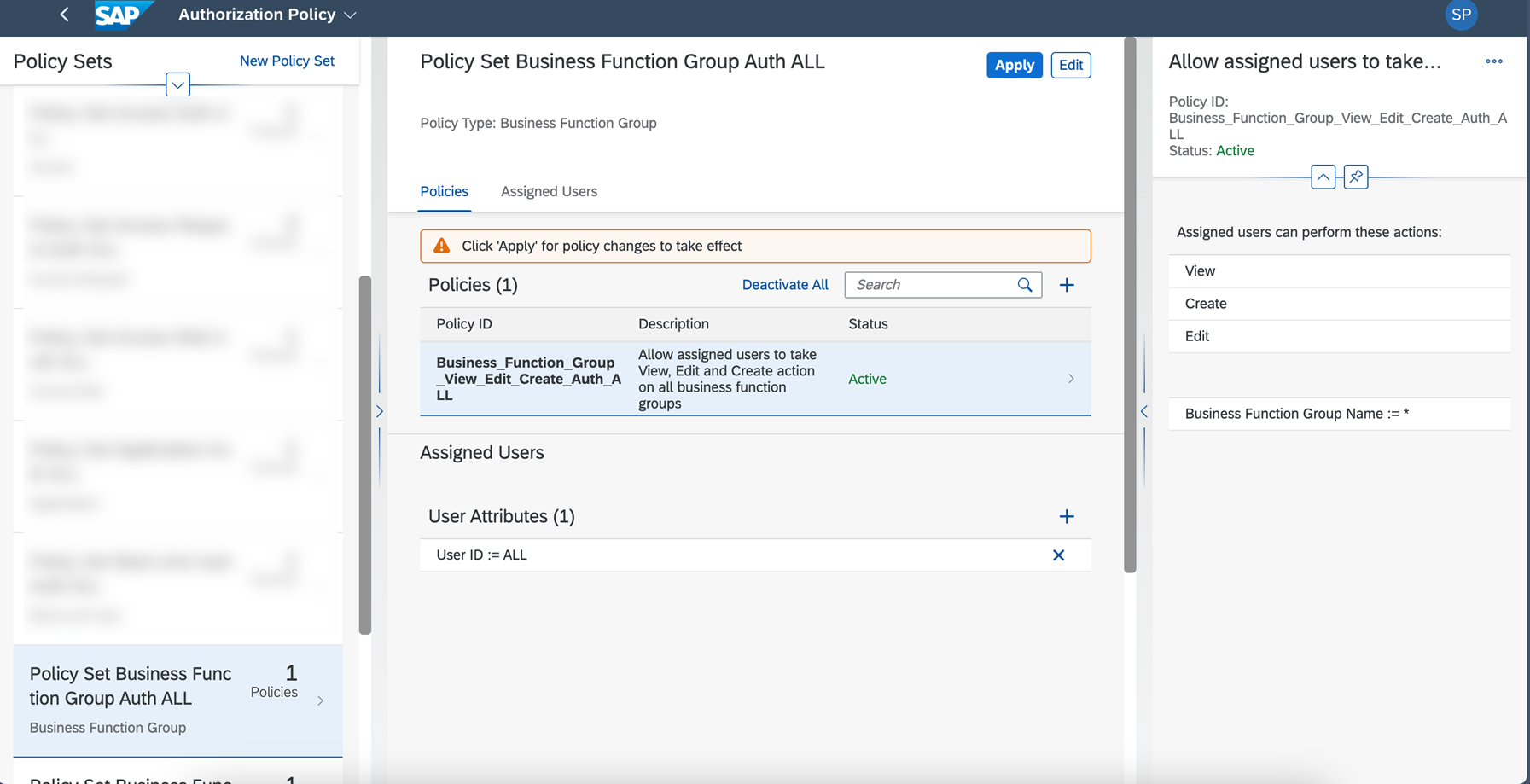
It’s often a requirement we want to place an authorization control based on data level security by selecting the authorization object attributes (the very popular and powerful feature of any SAP security architecture). Authorization Policy helps us to achieve it in SAP IAG.
We can perform authorization policies at different levels, starting with organization to the most granular level– the specific user id.
How to Set up an Authorization Policy?
Below are the steps which need to be followed in sequence to set up the authorization policy.
- Create policy set and assign users.
- Create policy.
- Assign task.
- Assign objects.
Some Examples of Using Authorization Policy
Use case 1 – Allow refinement process only for a specific user – based on risk and mitigation control mapping defined in authorization policy.

Use case 2– Restrict roles which are displayed in access request – based on application, Access/Application or Business Role an end user can search and request via Access Request Application

Use case 3- Deleting business function group- define which business function group an end user can delete via UI.
Conclusion – Like any other product offering of SAP infinite options are also available in SAP IAG and it’s all about the way we implement and use this functionality to solve a specific business problem.
DataNub Technologies with an extensive experience in IAG can help to solve a specific business program and can create a better value for the investments.

