Field Masking
Why Field Masking?
- Though it looks like swallowing a bitter pill - truth to be told - 67% of threat are originated from insider which in most cases are unattended.
- While there are couple of products available in market which focuses on cyber securities, we believe cyber security is not just hardware security & sap security - its inclusive of comprehended data security.
- We redesigned the entire data layer to bring extended data protection through our data masking and logging tools.
Who this solution for?
- Do you want to mask a sensitive field, even by allowing a Tcode to the user to view other information?
- Do you want to mask a sensitive field outside office hours, from an unknown system terminal?
- Do you want to build an additional control even if user has an access for transaction code?
How we developed it?
- Built using ABAP platform, our products does not require any additional add-on installation and licenses
- The product can be shipped via transports.
- The product is shipped with 20+ industrial best practice masking models.
- The product is compatible with S/4 HANA & ECC systems.
- The product can mask GUI, Webdynpro & Fiori Applications.
Making Data Useless for Hackers & Inside threats
- Data masking solves several critical threats – data loss, data exfiltration, insider threats or account compromise, and insecure interfaces with third party systems.
- Reduces data risks associated with cloud adoption, while maintaining many of its inherent functional properties.
- Allows sharing data with authorized users, such as testers and developers, without exposing production data..
- Can be used for data sanitization – normal file deletion still leaves traces of data in storage media, while sanitization replaces the old values with masked ones
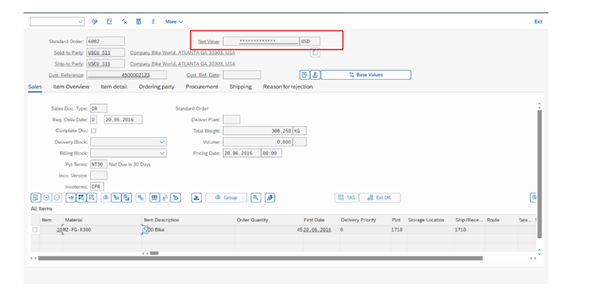
Use Case 1- We masked Net price field, though user has VA02 , he /she cant view net price value
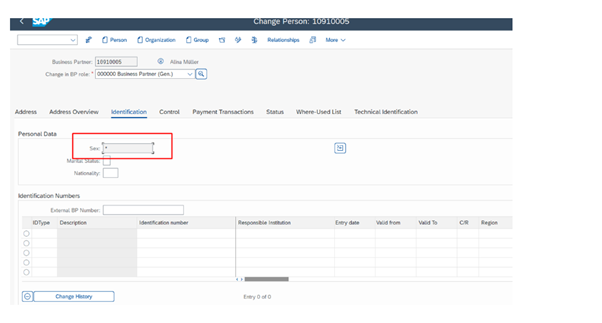
Use Case 2- We masked gender field in business partner, this will prevent any gender bias concern and empowers personal data protection
Few Other Insights
- Importance of Pseudonymisation
- According to the EU General Data Protection Regulation (GDPR), a new term has been introduced to cover processes like data masking, encryption, and hashing to protect personal data: pseudonymization.
-
Pseudonymization, as defined in the GDPR, is any method that ensures data cannot be used for personal identification. It requires removing direct identifiers, and, preferably, avoiding multiple identifiers that, when combined, can identify a person. In addition, encryption keys, or other data that can be used to revert to the original data values, should be stored separately and securely.
- Pseudonymization is a security technique that aims to protect sensitive data by replacing it with fictional data. Doing so it ensures that information cannot be directly linked to a specific individual without additional data, as Article 4 (5) of the GDPR outlines.
Latest Blogs & Case Studies

ABAP Code Generator
DataNub developed a solution to automate Report generation based on few patterns provided by end user.

Simplified DMS
DataNub DMS (Document Management System) is a cross-application module for managing documents in SAP. It offers the possibility to link documents to other SAP objects



